Compliance Certifications and Publicly Derived Control Coverage
Updated
by Calyssa Nowviskie
VISO TRUST automatically gathers evidence from the public web to help you understand a vendor’s likely security maturity — even before you request documentation. This evidence is used to generate control coverage in Risk Analysis.
What We Collect
- Compliance Certifications
If a vendor displays a SOC 2, ISO 27001, or other certification badge on their website or trust page, we detect and record it. - Public Artifacts
Security and privacy pages, audit summaries, policy documents, and other published materials are scanned to identify language about controls and practices.
How Control Coverage is Derived from Publicly Available Data
Publicly Available Artifacts
These are documents and materials that VISO TRUST can access in full, such as:
- Privacy policies
- Security whitepapers
- Trust portals
- Public audit summaries
- Policy documentation
Because we have direct access to these artifacts, we can:
- Detect security and compliance language.
- Map language to recognized control frameworks.
- Count these mapped controls as present in the vendor’s control coverage.
Compliance Certifications
These are compliance attestations that a vendor claims publicly (e.g., a SOC 2, ISO 27001, or PCI badge displayed on their website).
Because we don’t have access to the certification report itself, we:
- Recognize the certification claim.
- Use it to predict coverage for that framework.
- Count this coverage as partial credit toward the vendor’s controls.
This provides useful early insight but carries lower assurance than validated reports. To reduce residual risk, we recommend requesting the actual certification document (e.g., the SOC 2 report) from the vendor.
Controlling How We Use Compliance Certifications
Organizations can choose whether or not compliance certifications should influence residual risk and control coverage.
- An Org Admin can manage this setting under Settings > Risk model
- Toggle Include compliance certifications in risk calculations on or off.
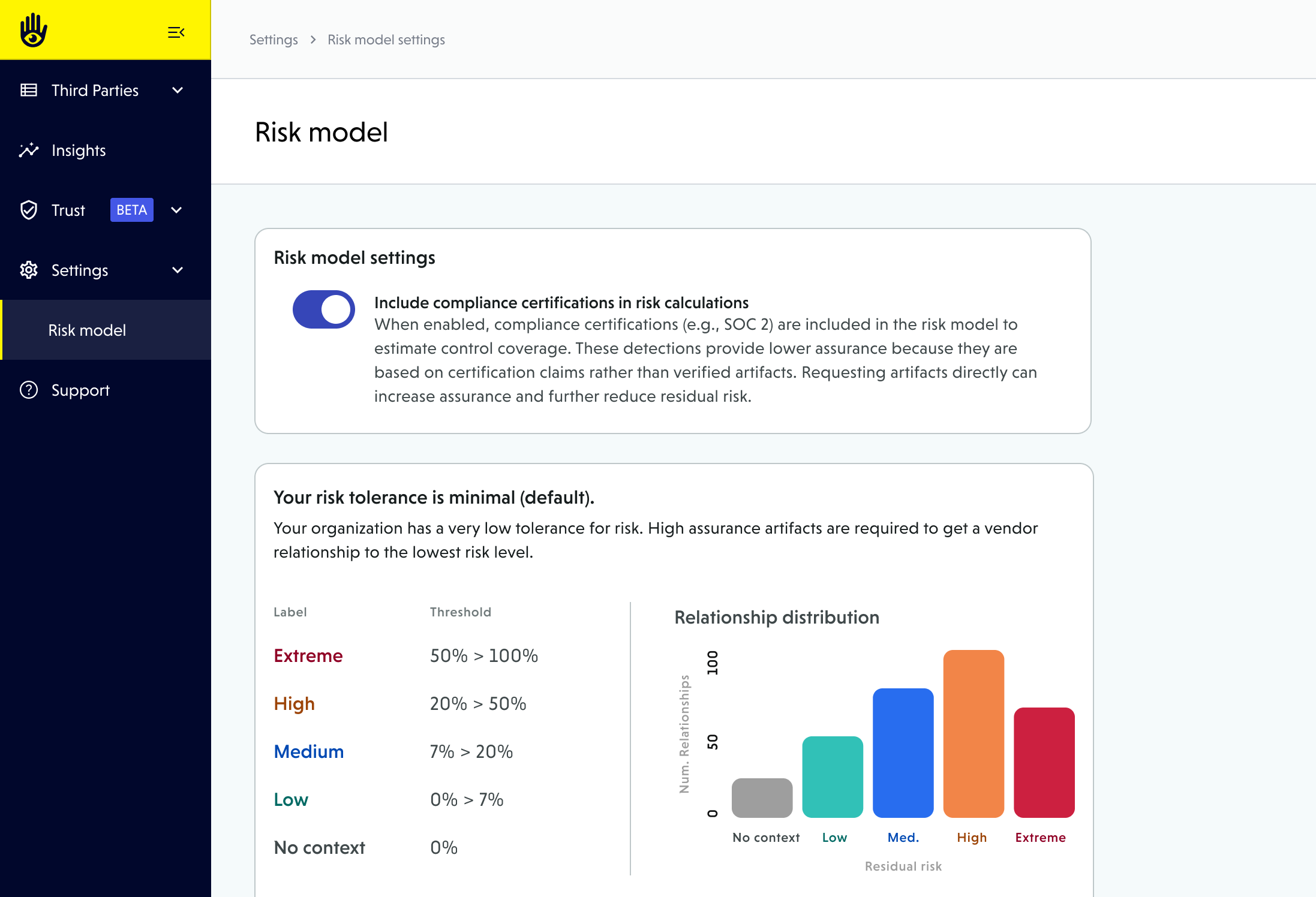
When enabled:
- Certifications like SOC 2 and ISO 27001 are included in risk calculations as partial control coverage.
- These detections provide lower assurance, since they are based on certification claims rather than verified artifacts.
When disabled:
- Controls tied to certification claims are excluded from coverage calculations.
- This may result in a higher predicted residual risk, since unverified controls will not be credited.
Requesting artifacts directly (e.g., a SOC 2 report) provides higher assurance and can reduce residual risk.
Reducing Risk
To fully evaluate a vendor’s risk, we recommend requesting the official compliance report (e.g., the SOC 2 report) through a collection request. This ensures your team has verified evidence beyond what is publicly visible.
