VISO TRUST Risk Assessment Process
Updated
by Tanya Tandon
VISO TRUST - Third Party Risk Assessment & Data Handling Process
- Platform Overview
VISO TRUST is a leading Third Party Risk Management (TPRM) platform that transforms how modern enterprises handle key vendor risks. Our platform extracts risk intelligence from documents, assets and networked information, delivering rapid and accurate assessments that empower organizations to innovate while mitigating risk. Traditional TPRM approaches often fall short, leading to ineffective risk management, but VISO TRUST offers a more robust solution.
Our AI-powered Artifact Intelligence analyzes risk-relevant information in just 10 seconds—work that would take an expert over 10 hours to do manually. This process relies on existing artifacts such as audits, config files and policy documents, ensuring efficiency and accuracy. Every assessment is reviewed by experts, with 24/7 escalation support available.
Built on the comprehensive VISO Risk Framework, which aligns with NIST 800-53, our platform covers essential risk dimensions like Security, Privacy, AI, Resilience and Product Security. We enhance this with network intelligence, aggregating data from various sources to provide a complete view of program risk.
- Process Overview
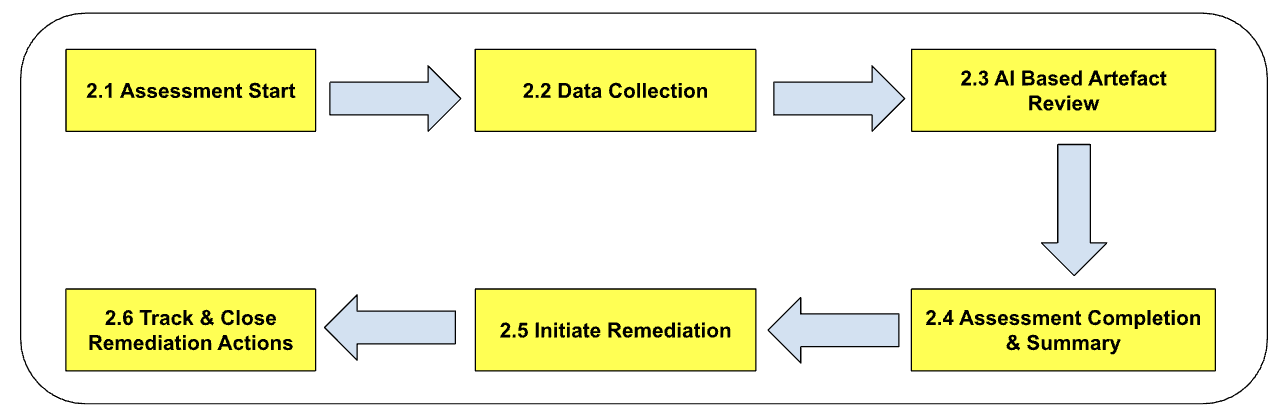
2.1 Start Assessment
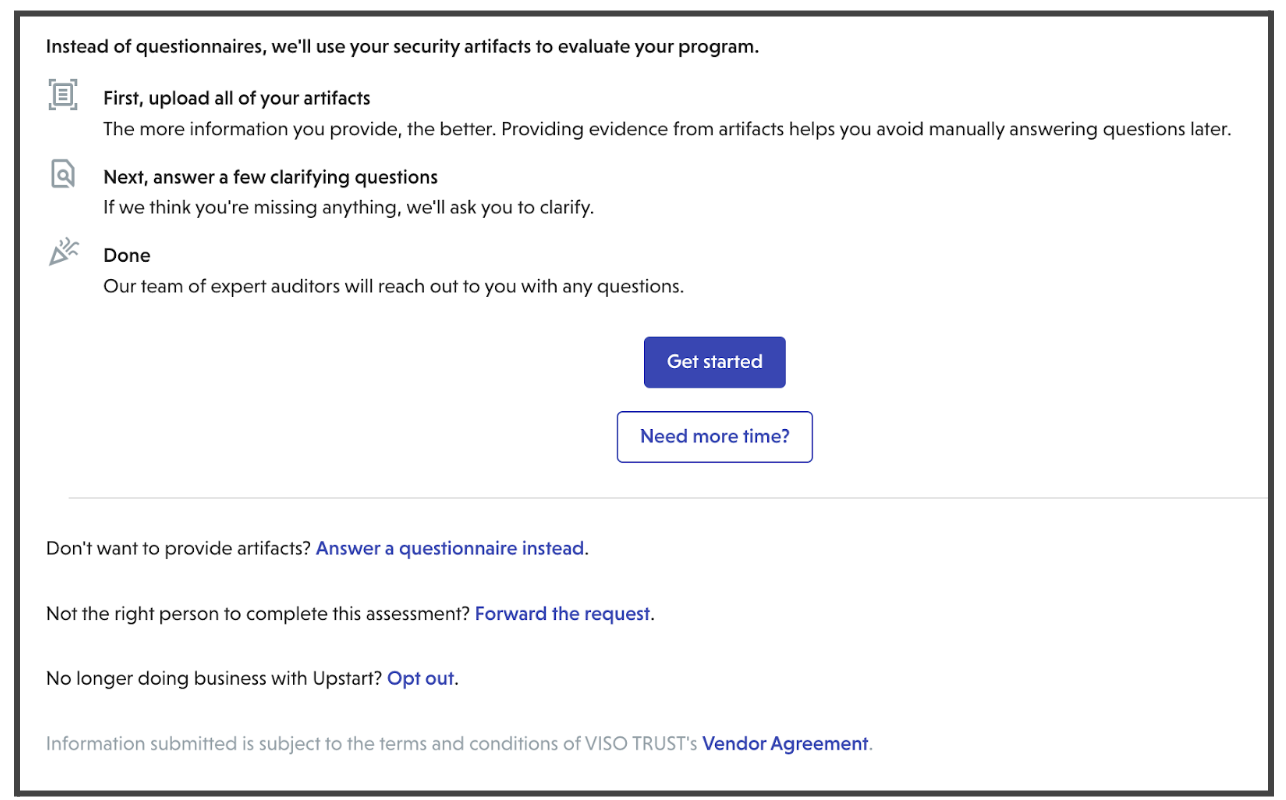
Once the onboarding of the vendors is complete, VISO TRUST enables the Client(s) to log into the portal and initiate an assessment. The third party receives an email from VISO TRUST with a passcode to access the secure portal. Vendors upload all security and privacy related documentation for the assessment in the portal. The process is self-explanatory, with easy navigation through different sections of the platform. The client selects the type of assessment, either interactive or non-interactive, based on the available documentation and the vendor's availability for involvement in later stages of the assessment.
2.2 Data Collection and Data Protection Measures
2.2.1 What Data Do We Collect?
VISO TRUST collects only the essential security and compliance documentation required to assess your organization’s risk posture. The data we typically request includes:
- Audit Reports: CSA STAR Level 2 Certification/Attestation Report, ISO 27001 Certificate and Statement of Applicability, HITRUST Certification/Validation Report, SOC 2 Type 2, BSI C5 report, PCI DSS Attestation of Compliance (on-site) and Responsibility Matrix, PCI DSS ROC and other similar certifications.
- Penetration Testing Results: Reports detailing any vulnerability assessments conducted.
- Privacy and Compliance Documents: Data Protection Agreements (DPA), Privacy Policies, and other related artifacts.
- Certificates of Insurance (COI): Proof of insurance related to cybersecurity and business operations.
- AI Trust Policies: For vendors utilizing AI, documentation regarding ethical AI practices and policies.
We do not collect any personal or unnecessary data beyond what is required for risk assessment.
2.2.2 How Is Your Data Collected?
Your data is securely uploaded to the VISO TRUST platform via encrypted portals. These portals allow vendors to upload documents directly, ensuring confidentiality. Additionally, our system can collect publicly available information (from websites, and trust portals) to supplement the data provided by your organization. All interactions with our platform, whether through branded client portals or public sources, are designed to prioritize security and ease of use.
2.2.3 How We Protect Your Data?
Your data’s security is our top priority. We maintain strict data protection practices, including:
- Encryption: All data is encrypted both in transit and at rest using industry-standard encryption protocols.
- Secure Storage: If you’re comfortable storing vendor data in platforms like Google Drive, you can trust that VISO TRUST provides even stronger safeguards through a purpose-built architecture designed specifically for sensitive third-party risk data.
- Access Control: Only authorized personnel have access to your data, governed by strict access controls to prevent unauthorized use or sharing.
Information submitted is subject to the terms and conditions of VISO TRUST's Vendor Agreement.
2.3 Artifact Review & Follow-up
Once uploaded, your data undergoes a multi-step analysis process:
- Artifact Intelligence: Our proprietary AI system, Artifact Intelligence, analyzes documents and other data sources to identify relevant security controls and potential risks. This allows for scalable and instant risk analysis across multiple types of artifacts, including documents, web pages, and API responses.
- Human Oversight: While AI ensures efficiency, human experts validate the results of the automated assessments, ensuring accuracy and alignment with security best practices.
- Follow-Up Questionnaire: Any missing pieces of information will be gathered through follow up questionnaires for validation
2.4 Assessment Completion and Summary Reports
All relevant assessment review output data is used to generate Client-Specific Risk Reports, which are shared with the requesting client. The summary report includes details of the assessments, identified gaps and recommendations to address those gaps, helping mitigate potential partnership risks. Vendor documents are never shared with any other client or third party without explicit consent.
2.5 Remediation Initiation and Closure
VISO TRUST platform allows the client to request remediation for recommendations provided to the vendor. The platform automatically triggers a remediation assessment, enabling the client to track the progress and closure of these recommendations.
- VISO TRUST - AI Integration benefits
3.1 Transparency in AI and Decision-Making:
One of the primary concerns surrounding AI is the potential for bias and irrational decisions. At VISO TRUST, our AI models are built to be transparent and explainable, ensuring that:
- Human-in-the-Loop Validation: Every risk assessment is reviewed by human experts, preventing sole reliance on automated decisions.
- Deterministic Risk Models: Our AI models are deterministic, meaning they follow clear, predefined rules, ensuring transparency in every decision. You can trace back every risk classification to the exact criteria and source material used.
- Continuous Monitoring and Learning: While our models are continuously refined, they are never trained using your specific data. Instead, we use pre-validated, anonymized datasets to enhance the model without compromising your data.
3.2 How AI Enhances Security at VISO TRUST:
Our AI architecture includes:
- Artifact Intelligence: This proprietary AI analyzes risk-related evidence from a variety of sources like documents, images, web pages, and API responses.
- Generative AI: We use secure infrastructure, such as Anthropic Claude, hosted via AWS Bedrock, ensuring enterprise-grade security while enhancing TPRM.
- Fine-tuned Models: Our AI models are trained on over 2.5 million pages and 800,000 labeled items, but never on your proprietary data.
3.3 What Makes VISO TRUST Stand Apart:
- Vendor Confidentiality: Your data remains confidential within the business relationship and is never shared with third parties without explicit consent. We also ensure that vendor data shared via our system is kept within the bounds of the relationship, preventing unauthorized access or misuse.
- Ethical Use of AI: Our AI models are designed to avoid bias or irrational decisions. By ensuring that AI-driven outputs are validated by humans, we mitigate any risks associated with biased AI behavior or hallucinations.
- Regulatory Compliance: VISO TRUST complies with global privacy regulations, including GDPR, CCPA, ISO 27001, and other prominent frameworks, ensuring your data is processed in accordance with the highest standards.
Contact Us:
For any questions or concerns about how we protect your data, reach out to us at support@visotrust.com.
