Getting Started
Updating a Vendor Assessment
How To Import New or Existing Relationships
Getting Started with Integrations in VISO TRUST
Assess a Vendor Instantly
Frequently Asked Questions
Understanding Assessment Results
Creating a Relationship
Knowledge Base
Implementation
Organization Settings
VISO TRUST Roles & Permissions
Notifications & alerts
Custom Organization Email Domain
Artifact Intelligence Trust Center
Netksope Application Risk Exchange Plugin
How to Create an API Access Token
How To Configure The VISO TRUST Netskope Application Risk Exchange (ARE) Plugin
How To Configure Coupa Supplier Sync
Customize branding for your organization
Relationships and Assessments
Auditor Review Summary
Assessment Phases
Risk Review and Remediation
Business Cases and Controls
Data Types and Impact
Questionnaires
Request vendor response to risk advisory
Configuring assessment defaults
VISO TRUST Agentic chat
Follow-up questionnaires
Continuous Monitoring
Vendor discovery
Understanding Subscribers and Default Subscribers
Sub-Processor Collection
Configuring relationship context
Vendor tiers
VISO TRUST Risk Assessment Process
Lifecycle Management for Relationships
Understanding Risk
Risk Advisories
Compliance Certifications and Publicly Derived Control Coverage
How VISO TRUST Risk Scoring Works
Customizing Risk Tolerance
Risk Network
Risk Calculations
Risk Insights
How the Risk Model Works
VISO TRUST API Documentation Guide
Product Updates
- All Categories
- Knowledge Base
- Understanding Risk
- Risk Network
Risk Network
 Updated
by Christian Coffey
Updated
by Christian Coffey
Risk Network
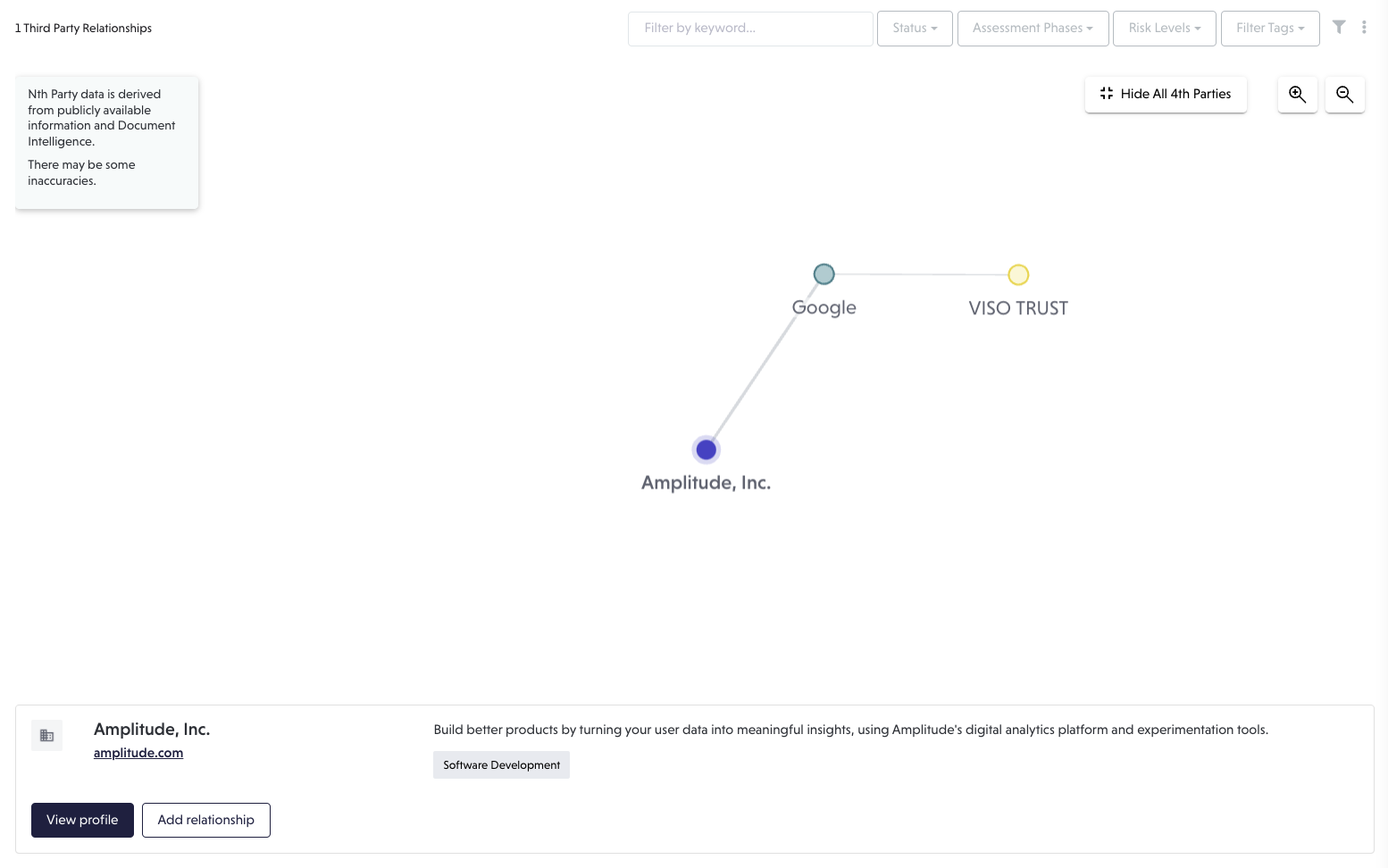
During an assessment, artifacts are analyzed and validated by both Artifact Intelligence and our team of expert auditors. These validations—though most notably used to compute risk—also contain valuable data that fuels other areas on the platform such as your Risk Network.
To start, navigate to the Relationships page and switch the toggle from List to Graph.
This is your Risk Network, a visual representation of your third and nth parties. By clicking any of the green nodes (third parties) you can reveal nth parties, which show in blue.
Click any nth parties to reveal information about that organization, create a relationship with them, and more!