CircleCI Incident
High Level Summary of the Security Advisory
CircleCI is a continuous integration and delivery platform that automates development workflows and IT operations.
On Jan 4 2023, CircleCI published a general statement about investigating a security incident. CircleCI updated the incident report on 13th January 2023, and revealed that an unauthorized third party leveraged undetected malware deployed to a CircleCI engineer’s laptop in order to steal a valid, 2FA-backed SSO session. Since the targeted employee had privileges to generate production access tokens as part of the employee’s regular duties, the unauthorized third party was able to access and exfiltrate data from a subset of production databases and stores, including customer environment variables, tokens, and keys. The last record of this unauthorized activity was noted to be December 22, 2022. Though all the data exfiltrated was encrypted at rest, the third party extracted encryption keys from a running process, enabling them to potentially access the encrypted data.
Should I be concerned?
Maybe. It depends on the relationship you have with CircleCI and other vendors.
Do you have an active relationship with CircleCI?
If yes, take the immediate corrective steps and incorporate security best practices, as recommended by CircleCI and outlined in the section (“What to do if you or your vendors were affected”) below.
Narrow the Scope
To start, we suggest understanding which of your vendors are using CircleCI. That being said, it is not necessary to ask every single vendor this question since you have defined a business case for all of your relationships. Since the attacker exfiltrated data from a subset of production databases and stores, including customer environment variables, tokens, and keys, the business case filters you can apply to your onboarded relationships are Data Transfer, Software/Hardware Supplier, Network Connection, and Data Storage.
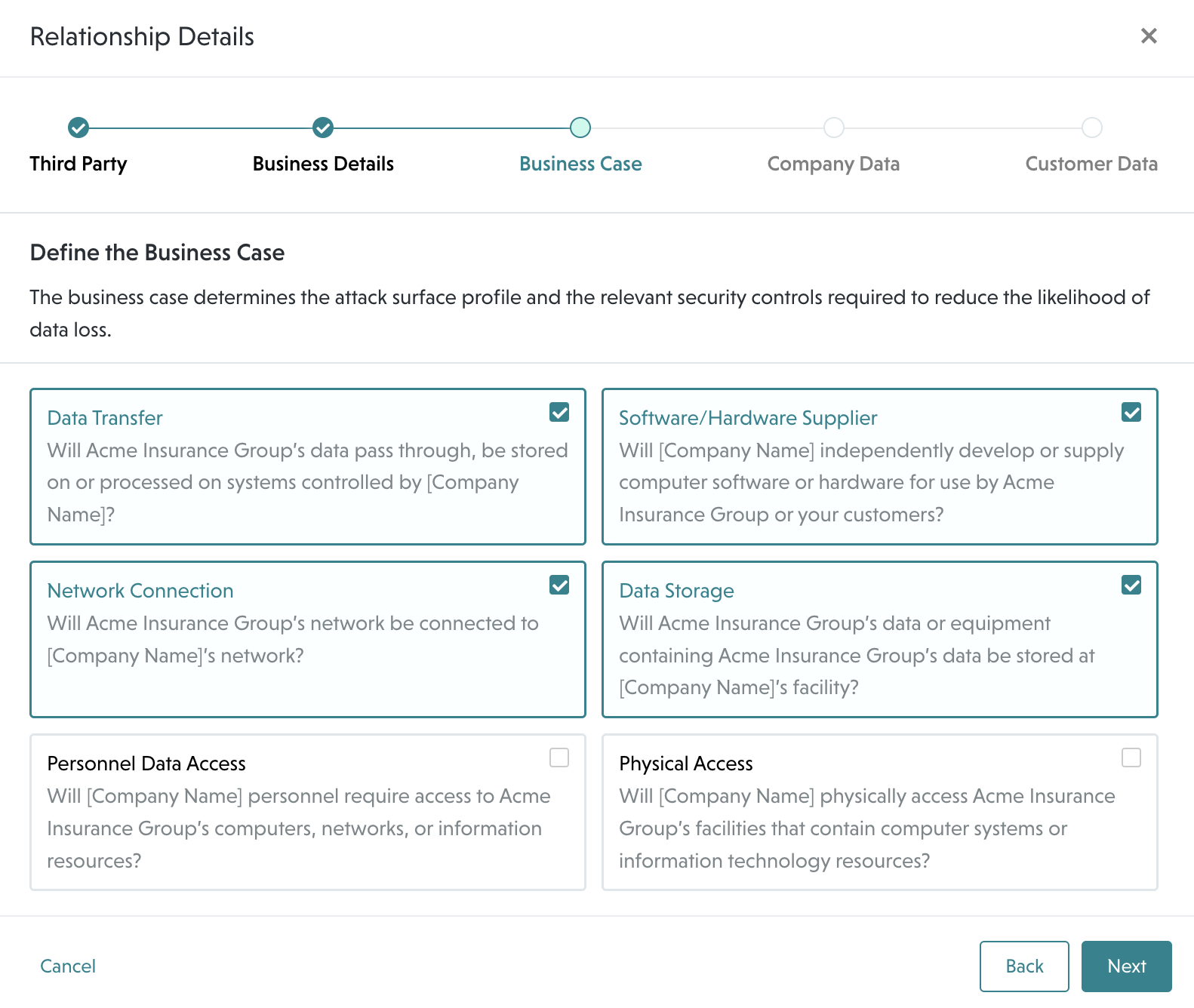
Click on the button below to see a list of your relationships that may be affected by the CircleCI incident.
Outreach
If your list of potentially impacted vendors is longer, we suggest prioritizing outreach based on the sensitivity of data shared with the vendor. Additionally, you can review the overall security posture of the vendor and the specific controls that can suggest whether or not a company is equipped to handle this type of incident:
Encryption of Customer Data (at rest), Encrypted Communication Over Public Networks (in transit), Vulnerability Management Program, Access Management Program.
Relationships where your organization has shared highly sensitive data (Extreme or High sensitivity) and a business case of Data Transfer, Software/Hardware Supplier, Network Connection and/or Data Storage with insufficient or Not Present controls in one or more of these areas suggest a higher risk for this incident.
What to do if you or your vendors were affected
CircleCI indicated as part of their Security Incident Report that appropriate remedial measures were taken internally to close the attack vector and add additional layers of security.
If you or your vendors are using the CircleCI platform, rotate any and all secrets stored in CircleCI immediately, and review internal system logs for any unauthorized access starting from December 21, 2022 through the date of completion of their secrets rotation.
A step by step guide for secret rotation including OAuth tokens, Project API Tokens, SSH keys, Project Environment Variables, Context Variables, User API Tokens, Runner Tokens have been published by CircleCI here.
In addition, CircleCI detailed security best practices on their Blog in order to strengthen the collective defense against inevitable future attempts including the use of OIDC tokens wherever possible, taking advantage of IP ranges to limit inbound connections, use of Contexts to enable automated rotation in a consolidated manner.
---------------------------------------------------------------------------
We are actively working on future product enhancements related to these types of events. If you found this information helpful or have additional feedback please let us know at product@visotrust.com.
For any additional questions, please reach out to your customer success manager.
The VISO Trust team
