CVE-2023-22515 - Broken Access Control Vulnerability in Atlassian Confluence Data Center and Server
Updated
by Keith Kirkland
High Level Summary of the Security Advisory
Atlassian Confluence is a collaboration and documentation tool developed by Atlassian that enables teams and organizations to create, share, and collaborate on content, knowledge bases, and documentation in a centralized online space. Atlassian is a leading software company offering a suite of tools and solutions designed to enhance project management, streamline issue tracking, and support software development.
On Oct 4, 2023 Atlassian Corporation (Atlassian), issued an advisory regarding vulnerability identified in Atlassian Confluence Data Center and Server versions.
As per the advisory, Atlassian has been made aware of a reported issue by a few customers where external attackers may have exploited a previously unknown vulnerability in publicly accessible Confluence Data Center and Server instances to create unauthorized Confluence administrator accounts and access Confluence instances. Further, Atlassian has evidence to suggest that a known nation-state actor is actively exploiting CVE-2023-22515 and that the company (Atlassian) continues to work closely with our partners and customers to investigate. The severity level of this vulnerability has been classified as Critical with a CVSS score of 10, according to the severity scale published by Atlassian.
The Confluence Data Center and Server versions listed below are affected by this vulnerability. Atlassian has recommended customers using these versions to proceed with upgrading their instances without delay.
Product | Affected Versions |
Confluence Data Center and Confluence Server |
|
Versions prior to 8.0.0 are not affected by this vulnerability.
Should I be concerned?
Maybe. It depends on if you have a relationship with Atlassian. Click on the link below to find out if you have a relationship with this vendor. If you do, follow the recommendations below.
Note: this link specifically references vendor directory records. You may also want to search your Relationship List for "Atlassian” to confirm.
What to do if you have an active relationship with Atlassian
As per the advisory, Atlassian Cloud sites remain unaffected by this vulnerability. If your Confluence site is accessible through an atlassian.net domain, it is hosted by Atlassian and is not susceptible to this issue.
Atlassian has recommended upgrading each of the affected installations to one of the listed fixed versions or to any later version from the list below
Product | Fixed Versions |
Confluence Data Center and Confluence Server |
|
For a full description of the latest versions of Confluence Data Center and Confluence Server, kindly refer the release notes, here. You can also download the latest version from Atlassian download center, here.
Atlassian has outlined the following mitigation steps:
- Upgrade to a fixed version (See: Upgrade Instructions)
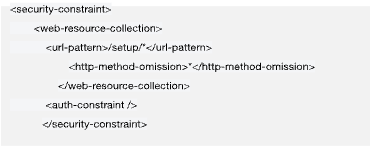
Customers with Confluence Data Center and Server instances accessible to the public internet including with user authentication, should restrict external network access until you can upgrade. If you cannot restrict external network access before your upgrade, apply the following interim measures to mitigate known attack vectors by blocking access to the /setup/* endpoints on Confluence instances. This is possible at the network layer or by making the following changes to Confluence configuration files.- On each node, modify
/<confluence-install-dir>/confluence/WEB-INF/web.xmland add the following block of code (just before the</web-app>tag at the end of the file) - Restart Confluence
This action will block access to setup pages that are not required for typical Confluence usage, for further details see the Atlassian FAQ page- Atlassian has included a note emphasizing that these mitigation actions are limited and are not a replacement for upgrading instance; and to perform the upgrade as soon as possible.
- On each node, modify
- Threat detection
Atlassian cannot confirm if your instances have been affected by this vulnerability. They have advised you to work with your security team to check all affected Confluence instances for evidence of compromise, as outlined below. If any evidence is found, you should assume that your instance has been compromised and evaluate the risk of flow-on effects. If your Confluence instances have been compromised, these threat attackers hold full administrative access and can perform any number of unfettered actions including - but not limited to - exfiltration of content and system credentials, and installation of malicious plugins.
Evidence of compromise may include:
- unexpected members of the confluence-administrators group
- unexpected newly created user accounts
- requests to
/setup/*.actionin network access logs - presence of
/setup/setupadministrator.actionin an exception message inatlassian-confluence-security.login the Confluence home directory.
If you believe you were compromised, please raise a request at atlassian support request as Atlassian assistance is required to recover and protect your instance.
Atlassian has provided a FAQ page offering valuable supplementary information.
--------------------------------------------------------------
We are actively working on future product enhancements related to these types of events. If you found this information helpful or have additional feedback please let us know at product@visotrust.com.
For any additional questions, please reach out to your customer success manager.
Stay ahead of the curve with our Public Risk Notice Alerts!
Get the latest information and news to your inbox on cybersecurity breaches and third-party vendor risks that could impact your organization.
Sign up today to fortify your organization's security.
The VISO TRUST team
—----------—----------—-----