OpenSSL Vulnerability
High Level Summary of the Security Advisory
On November 1, 2022, the OpenSSL Project released a security advisory detailing a high-severity vulnerability in the OpenSSL library. The vulnerability is tracked as CVE-2022-3602.
The vulnerability is a memory corruption bug that can be triggered when a vulnerable client or server validates an X.509 certificate. A specially crafted email address abusing non-ASCII codepoints in a client or server certificate could exploit this vulnerability to achieve denial of service (DoS) or remote code execution (RCE).
Should you be concerned?
Maybe. It depends on the relationship you have with your vendors.
Encryption in Transit and Vulnerability Management are two of VISO Trust’s Security Control Domains that cover controls implemented to remediate or prevent this flaw. These domain’s are considered in scope for the following business cases: Data Transfer, Network Connection, and Software/Hardware Supplier.
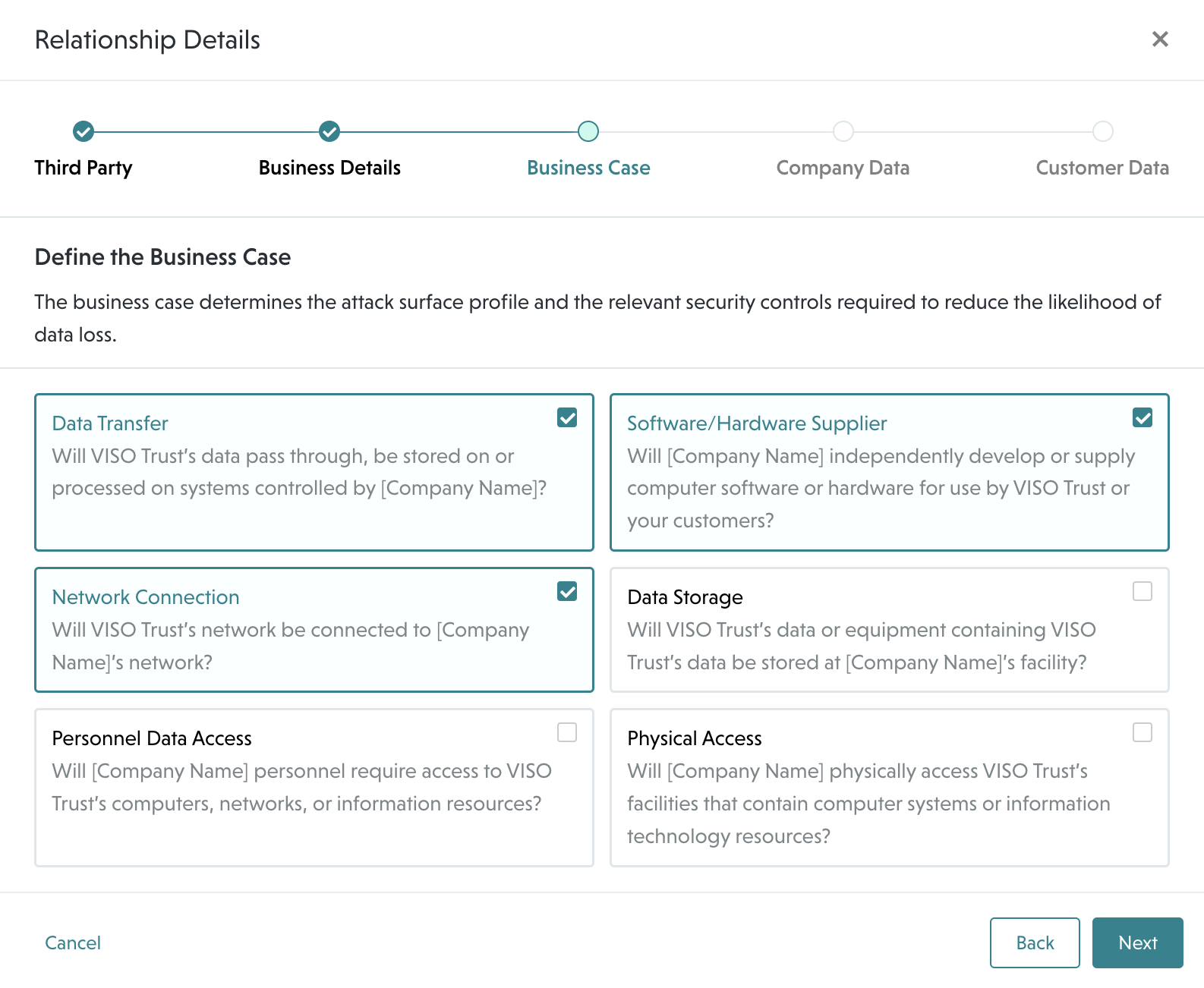
Click on the button below to see a list of your relationships that may be affected by the OpenSSL vulnerability.
To do this manually, select Data Transfer, Network Connection, and Software/Hardware Supplier in the Business Case filter on your Relationships list page or Risk Insights dashboard to understand more about the potential impact to your organization.
What should your vendors do if they were affected?
If your vendors are using OpenSSL from 3.0.0 to 3.0.6 included on systems which may interact with your company or customer sensitive data, they should upgrade to 3.0.7 in order to remediate the risk of these types of attacks.
High severity vulnerabilities like this should be mitigated as part of a mature vulnerability management program for all organizations.
--------------------------------------------------------------------------------------------------
We are actively working on future product enhancements related to these types of events. If you found this information helpful or have additional feedback, please let us know at product@visotrust.com.
For any additional questions, please reach out to your customer success manager.
Thanks for your continued support!
The VISO Trust Team
